
From the endpoint to the network, Somansa can monitor and record all sections of the company's confidential and personal data to prevent outside leakage. Somansa DLP solutions can be deployed in either a cloud version or an on-premises version.
Identification of company's data security status
Minimize the risk in case of a data breach by storing
minimum personal data through scanning, destroying, or encrypting unattended personal data on the PC and deleting
unnecessary personal information files.
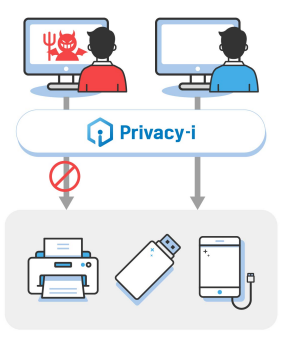
Protect data by controlling and recording endpoint(PC)
events where information can be leaked to printers, removable storage media, messenger, WebMail, and cloud.
Somansa Privacy-i monitors and scans for confidential data on desktops and laptops based on pre-defined and customizable content-aware detection methods and policies.

- >> Scans and locates sensitive data on desktops and laptops based on content-aware detection methods and policy rules.
- >> Monitors/Blocks copying and saving/downloading of confidential files based on policy rules.
- >> USB drives, CDs/DVDs, and other removable storage devices.
- >> Wi-Fi, Bluetooth, Airdrop, Thunderbolt, and Printing.
Data Loss prevention
For effective confidential data loss prevention, it is necessary to accurately detect the data when they are copied, moved and/or transmitted. To verify the accuracy of the patterns and ensure credibility of detection results, Privacy-i verifies the validity through checksum tests. Since custom patterns can also be generated as well as patterns regulated as PII by the laws, an organization can register and execute confidential data patterns that fit its needs.
Through Privacy-i, users can search and categorize information formats for confidential data stored in endpoint devices by themselves. Also, the administrator can remotely inspect for the organization's inspection policy in accordance with the security policy and manage logs at the center console. Validity date could be set for files detected to be Diagnosis” containing important data, or they could be encrypted or permanently deleted to block leakage risks
Privacy-i supports about 300 file formats for the inspection including well-known office document formats such as MS Office and PDF, as well as compressed files. Even when a user attempts to bypass the security policy by manually modifying the file extension, Privacy-i can detect the original file format and also analyze for encrypted files, OLE inserted files, hidden files, etc.
DLP+Center is an integrated platform service where content-based policies are configured and managed and audit logs are reported to. Through DLP+ Center, administrators can configure and apply network DLP policies and manage events through reporting and dashboard. Dashboard provides data related to personal data retention status and loss routes per department or user.
Privacy-i is compliant with regulations regulated by the Privacy Act and Information Communication Network Act such Ensuring Personal Data Safety and Technical Mangerial Protection Measures. Therefore, any organization retaining personal data such as information communication service companies, financial organization, and public enterprises can utilize Privacy-i.
Privacy-i can adjust the CPU allocation that it takes when detecting endpoint devices retaining confidential data and ensures a certain level of performance so that the user can smoothly focus on business processes
Privacy-i Prevent, through the agents installed in endpoint devices, control files containing personal & confidential data when they are being printed, transmitted, written in body contents, and/or copied to USBs in accordance with the organization's security policy.
Data Loss Channel Control

Copy Prevent
Copy Prevent content-based controls numerous types of portable storage devices within the organization
Print Prevent
Print Prevent allows or blocks and logs printing of documents containing confidential data in accordance with the organization’s security policy.
Media Control
Media Control provides control features that including allowing or blocking data moving through media such as wireless LAN, data network, and Bluetooth. For CD/DVD, reading/writing is blocked based on its content.
